Coming Soon!
Network XDR
XDR (Extended Detection and Response)
Cyber threats are evolving, and small businesses need enterprise-grade protection with less complexity and lower costs.


Smart, automated security with real-time threat intelligence feeds – simplifying cybersecurity for growing businesses.
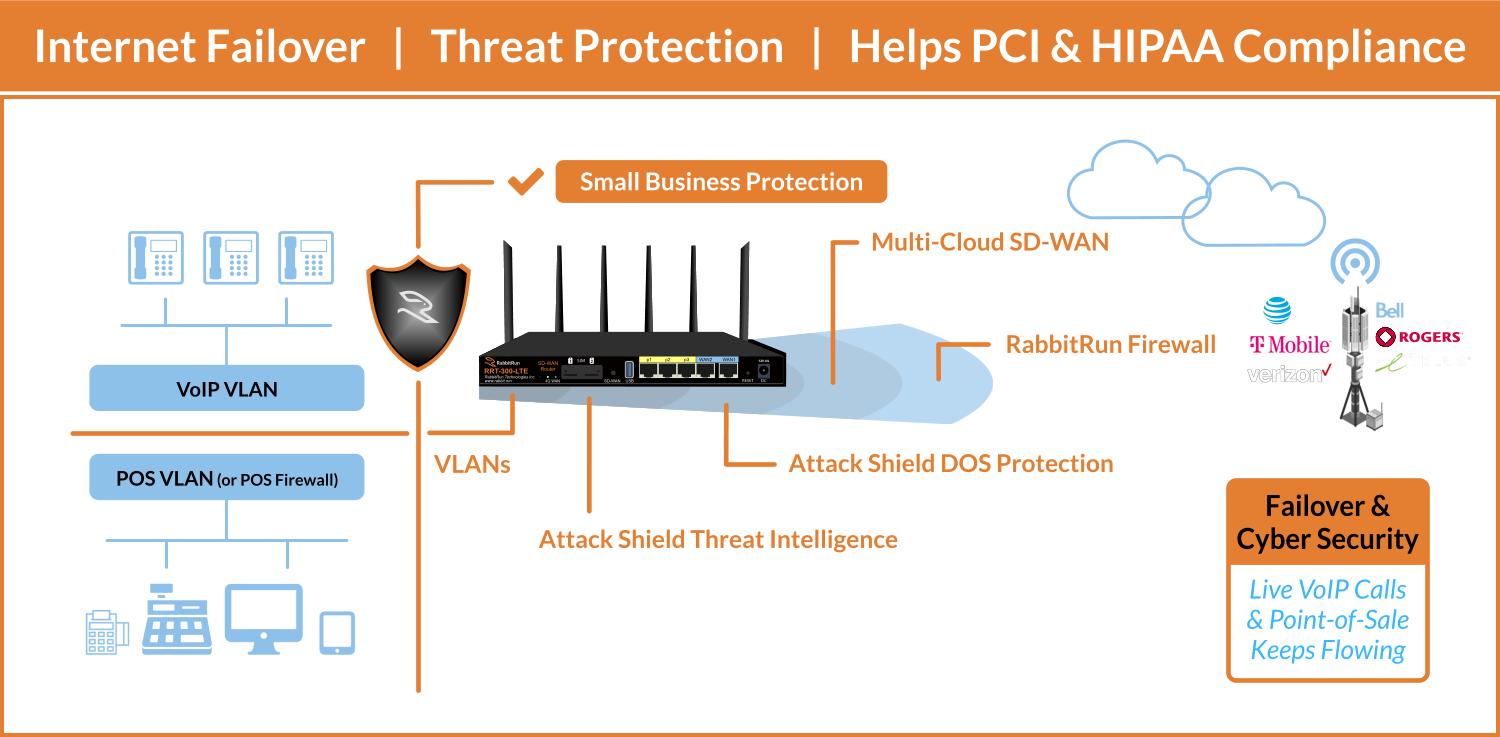
Become A Valued Partner
IF YOUR CUSTOMERS ARE LOOKING FOR
“ALWAYS ON VOICE & POS”, WE HAVE THE SOLUTION!


